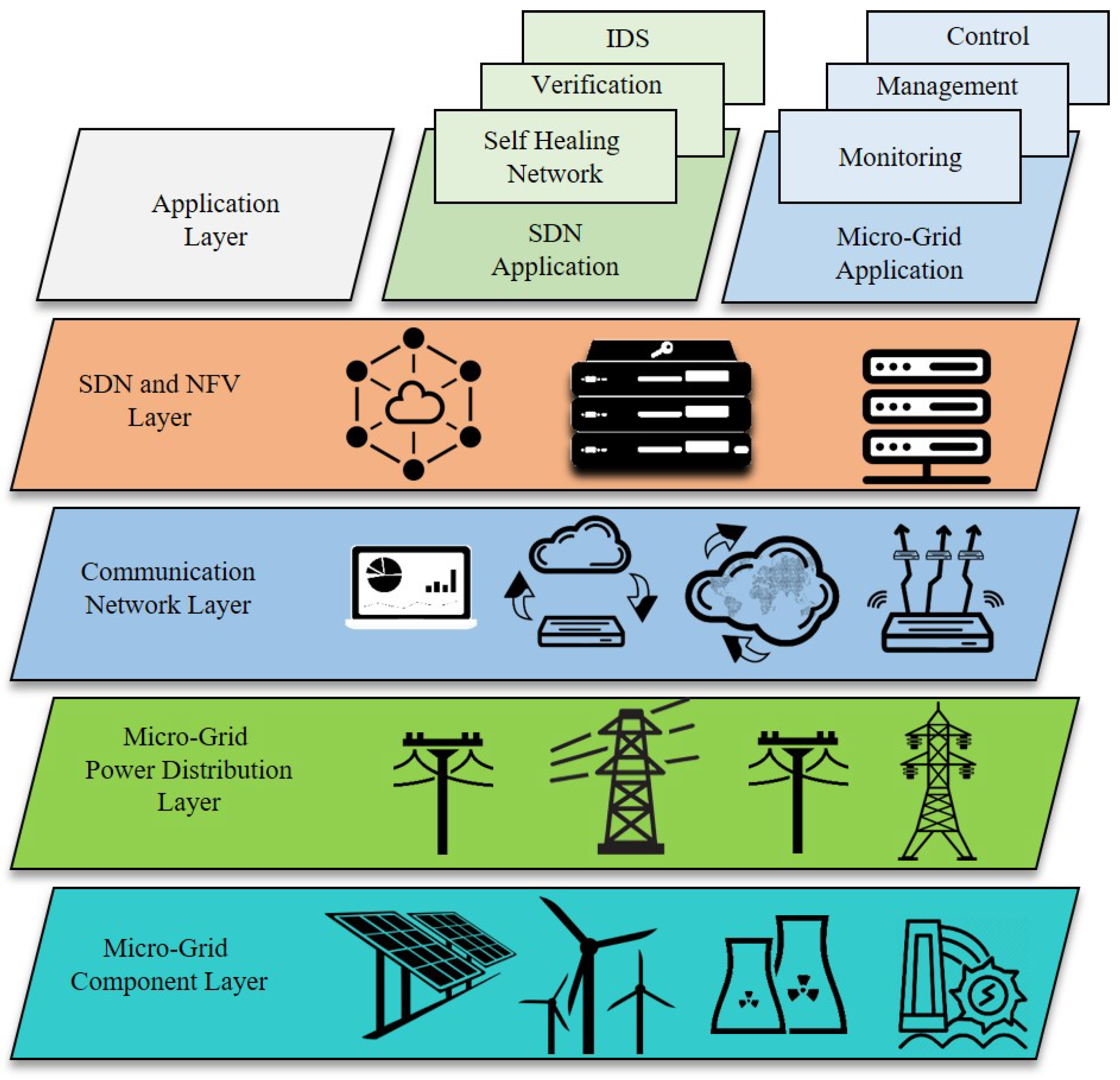
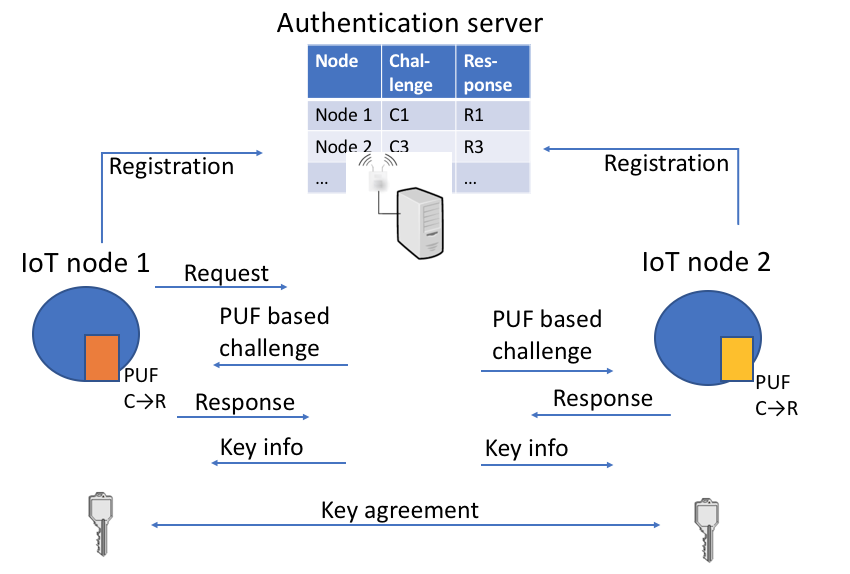
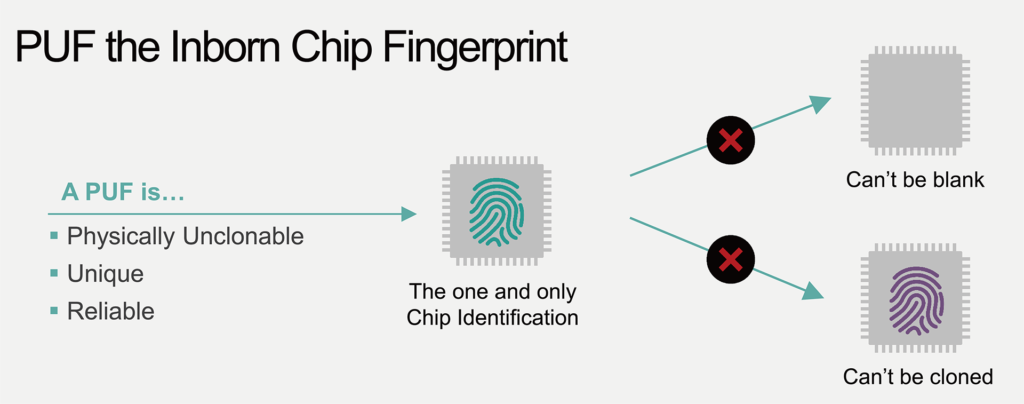
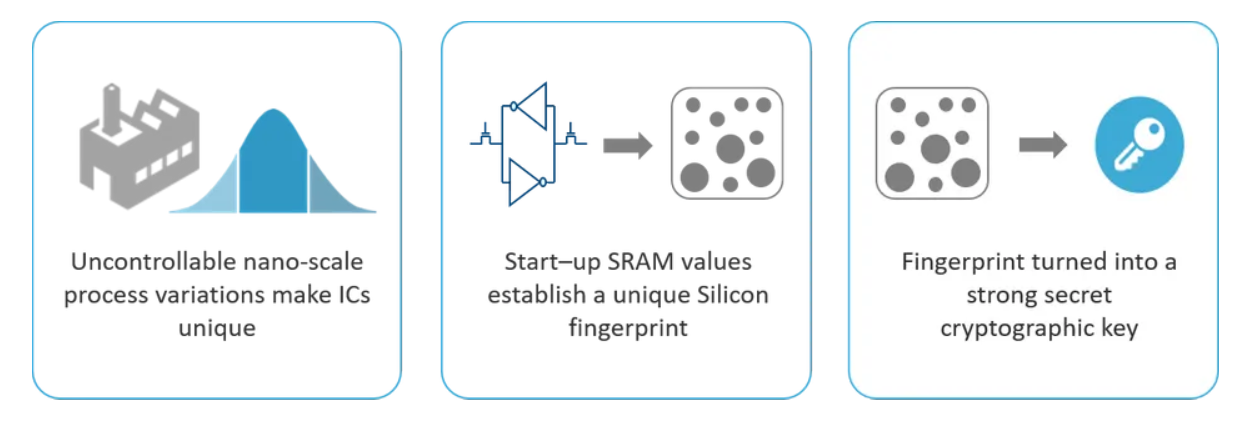
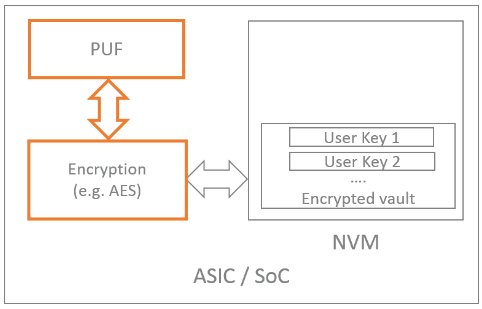
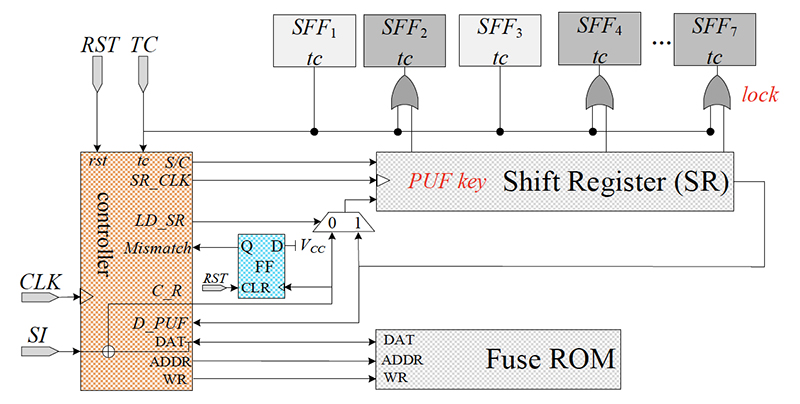
A survey on physical unclonable function (PUF)-based security solutions for Internet of Things - ScienceDirect

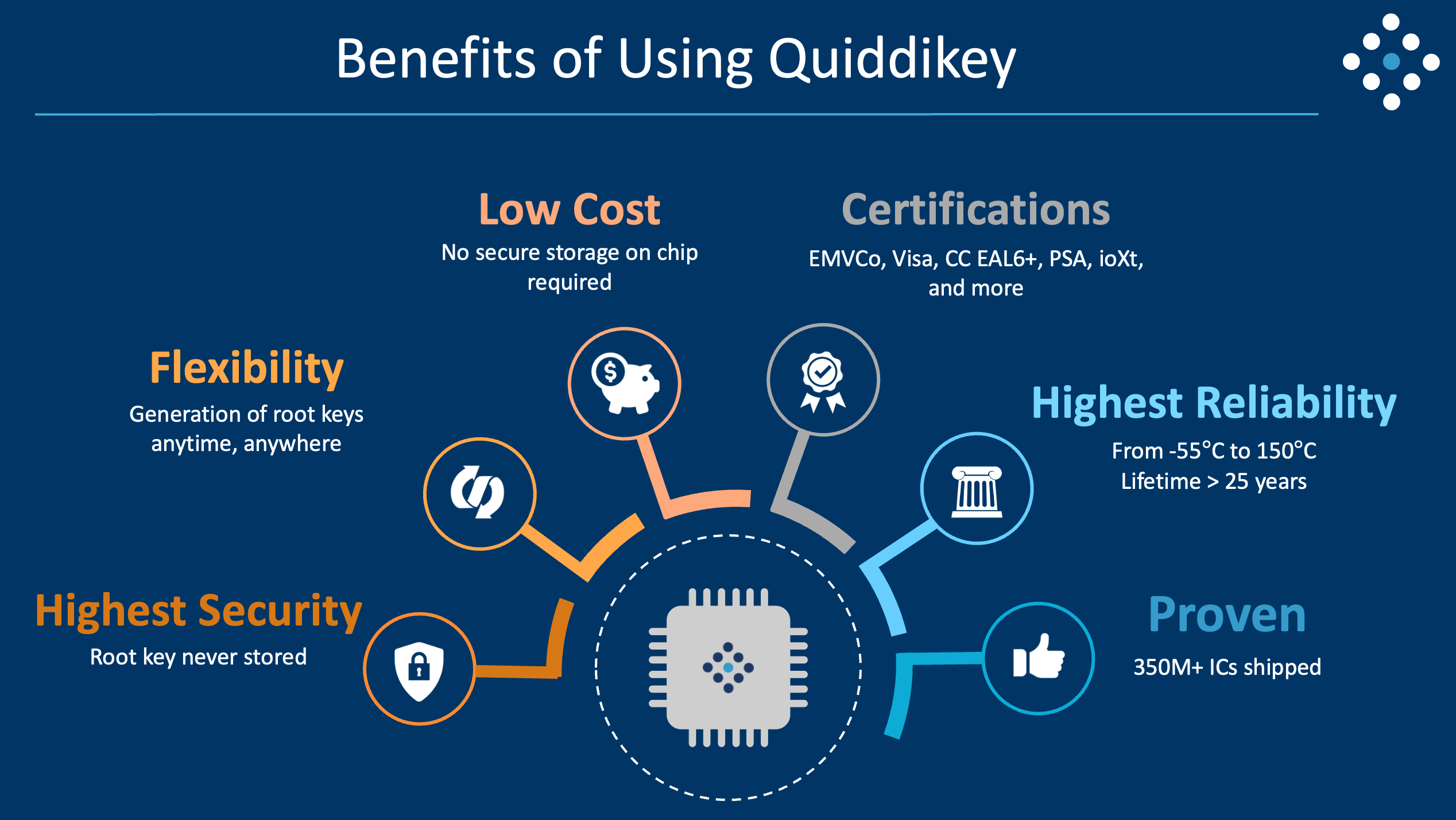
Startup PUFsecurity's PUF-based Crypto Coprocessor Receives Accolade at EE Awards Asia 2022 - EE Times Asia

Nanoscale physical unclonable function labels based on block copolymer self-assembly | Nature Electronics